What the latest fines mean for eHealth
The UK ICO has fined British Airways and Marriott a total of 320 million Euro. The scale of the fines has profound implications for every business. Here, we look at how this highlights the importance of GDPR technical measures, and the impact on eHealth.
In the past few weeks, the UK ICO has issued unprecedented fines to BA and Marriott totalling 320 million Euro. These fines dwarf all previous GDPR-related fines and have profound implications for every business. In both cases, the companies had shortcomings related to GDPR technical measures. In this blog, we will look at why the fines were so high and what specific lessons can be learned by eHealth companies.
What happened?
In September last year, British Airways announced that they had identified a serious cyber attack affecting their online payments. This attack involved hijacking the payment gateway and redirecting customers to a fake site to harvest their details. During the course of investigations, it became clear that round half a million customers had their credit card and personal details stolen over a 3 month period.

The Marriott case is a bit more complex. In 2014, hackers accessed the customer database of the Starwood hotels group and, over time, were able to steal details of 339 million customers. Marriott acquired Starwood in 2016, but didn’t identify the ongoing attack until November 2018.

What has the UK Information Commissioner’s Office (ICO) said?
The ICO’s investigation found that Marriott failed to undertake sufficient due diligence when it bought Starwood and should also have done more to secure its systems. With British Airways, they found that a variety of information was compromised by poor security arrangements at the company, including log in, payment card, and travel booking details as well name and address information. In other words, in both cases, GDPR technical measures were insufficient.
The Information Commissioner Elizabeth Denham said:
“Personal data has a real value so organisations have a legal duty to ensure its security, just like they would do with any other asset. If that doesn’t happen, we will not hesitate to take strong action when necessary to protect the rights of the public.”
Why are the fines so huge?
GDPR allows data protection authorities to issue fines of up to €20M, or 4% of a company's global turnover for the previous year, whichever is higher. If you are a company with a multi-billion turnover, this quickly leads to fines of this level.
For multinationals, GDPR also allows one data protection authority to take the lead on behalf of all the others. This is referred to as the “one stop shop” process. In both these cases, the fines are being levied by the ICO on behalf of all 31 member countries in the EEA and will be shared between them.
How could this affect you?
Every organisation that handles personal data needs to make sure they comply with data protection legislation. Both these cases highlight the importance of proper implementation of GDPR technical measures including data security and access control. Importantly, this obligation also applies when a company’s assets are transferred to another company. This could have really profound implications for startups as it will affect the due diligence done by investors and buyers.
For years, we have known that financial information needs to be protected against theft. But nowadays, health information can be even more valuable to hackers than payment or other personal information. Therefore, you could well be vulnerable to the same sorts of attack.
How to protect yourself
GDPR is deliberately vague on exactly what technical measures you should adopt. However, if you are processing sensitive "special" data, there are certain minimum requirements you must meet. These include ensuring good data security, proper access controls, using strong record-level encryption and applying pseudonymization. It is also essential that you log all data transaction in an immutable audit log.
One way to assess your system security is to imagine what damage a hacker can do with a given set of login details. For instance, can they dump your database and access all the records? Or can the data only be decrypted on your actual server. Can they hijack a vital subsystem and redirect traffic to their own server? Can they easily link health records with personal IDs? This should form the basis of your data protection impact assessment (DPIA).
How we solve the issue
Here at Chino.io, we specialise in data security and data protection for health data. We can assess your overall data protection compliance, as well as providing a comprehensive API for compliant health storage.
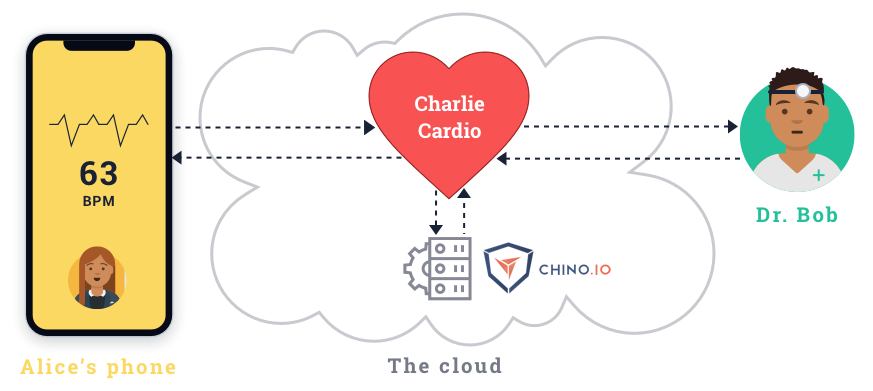
Our service is suitable for any digital health application, including those covered by the new Medical Device Regulation (MDR). Correctly implementing these GDPR technical measures is challenging. Using our service, you get a guarantee of compliance, and save significant time, money and effort. You can read much more about this in our eBook on building GDPR and HIPAA compliant applications.








